Qubes-Whonix 14.0.0.6.9 TemplateVMs for R3.2 and R4–Testers Wanted!
(Note: This page is a Draft waiting for review by Patrick)
Qubes-Whonix only!
For this testers wanted task, users should create fresh Whonix VMs.
Installing the R3.2 or R4.0 testers Qubes-Whonix 14 TemplateVMs.
Step 1: Clone existing whonix-gw and whonix-ws templates. It is recommended the newly cloned VMs be given names such as whonix-gw-13 and whonix-ws-13. This is to prevent new templates from being confused with other Whonix templates.
Step 2: Change all VMs based on whonix-ws and whonix-gw templates to the newly cloned templates.
Step 3: Remove the current whonix-gw and whonix-ws Qubes-Whonix templates.
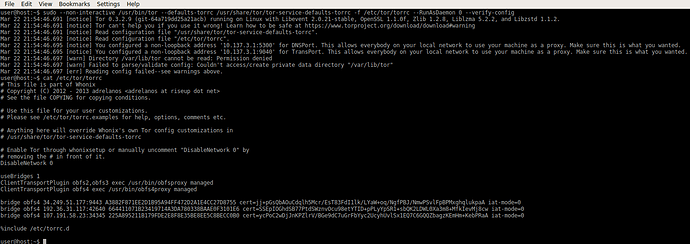
In dom0, run.
sudo dnf remove qubes-template-whonix-gw
sudo dnf remove qubes-template-whonix-ws
Step 4: Reinstall whonix-gw-14 and whonix-ws-14 Qubes-Whonix templates release candidate versions.
- Warning: Reinstalling Whonix templates while using
sys-whonixas the updateVM could take hours given the 1.2 GB total to download. It may be preferable to change the Global Setting in Qubes VM manager to temporarily usesys-firewall. Qubes will then download updates over clearnet and the operation will likely take less than an hour.
In dom0, run.
sudo qubes-dom0-update --enablerepo=qubes-dom0-unstable qubes-template-whonix-gw-14 qubes-template-whonix-ws-14
-
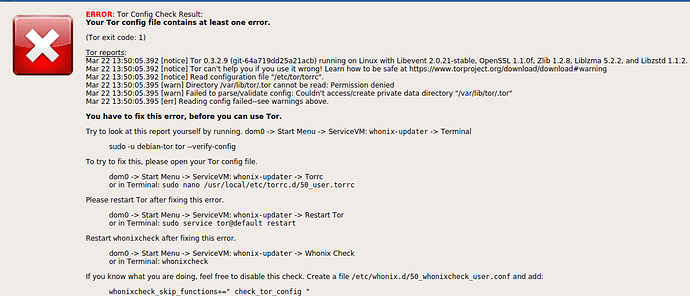
Qubes R3.2 note - users might encounter
tarerrors relating to dom0-updates folder not existing insys-whonix(if updates are downloaded over Tor) orsys-firewall. If this is the case, before downloading Whonix templates with the command above, the following command should be run in either thesys-whonixorsys-firewallupdateVM.In updateVM Konsole, run.
sudo mkdir -m 775 /var/lib/qubes/dom0-updates
sudo chown user:user /var/lib/qubes/dom0-updates
Step 5: After re-installling templates, clone the whonix-gw-14 and whonix-ws-14 template VMs and name them whonix-gw and whonix-ws.
- Note: This step is necessary if
saltis to be used in step 8 to createsys-whonixandanon-whonixVMs.
Step 6: (Optional ) Users can remove whonix-gw-14 and whonix-ws-14 templates. However, retaining clean Whonix 14 template VMs for later testing may be desirable.
In dom0, run.
sudo dnf remove qubes-template-whonix-gw-14
sudo dnf remove qubes-template-whonix-ws-14
Step 7: Update[1] whonix-gw and whonix-ws template VMs.
The following should be applied in both template VM Konsoles.
sudo apt-get update && sudo apt-get dist-upgrade
Step 8: After updating templates, recreate Whonix VMs from Qubes VM Manager. Optionally, advanced users can create Whonix VMs using salt[2][3].
Create VMs from Qubes VM Manager.
Qubes R4.0
-
Create
sys-whonixVM.Qubes VM Manager→Qube→create a new qube.-
Create new VM with these settings.
Name and label:
sys-whonix-14( purple )
Type:AppVM
Template:whonix-gw
Networking:sys-firewall
Advanced:provides network(check)
-
* Create `anon-whonix` VM
`Qubes VM Manager` -> `Qube` -> `create a new qube`.
* Create new VM with these settings.
Name and label: `anon-whonix-14` ( purple )
Type: `AppVM`
Template: `whonix-ws`
Networking: `sys-whonix-14`
Advanced: `n/a`
Qubes R3.2
-
Create
sys-whonixVM.Qubes VM Manager→Qube→create a new qube.-
Create new VM with these settings.
Name and label:
sys-whonix-14( purple )
Type:ProxyVM
Template:whonix-gw
Networking:sys-firewall
-
* Create `anon-whonix` VM.
`Qubes VM Manager` -> `Qube` -> `create a new qube`.
* Create new VM with these settings.
Name and label: `anon-whonix-14` ( purple )
Type: `AppVM`
Template: `whonix-ws`
Networking: `sys-whonix-14`
( Optional ) Create Whonix VMs using salt. Advanced users only!
Users have the option of using salt to recreate sys-whonix and anon-whonix VMs. Since no two VMs can have identical names. It would require any current Whonix-13 based sys-whonix or anon-whonix VMs to be renamed prior to using salt.
In dom0, run.
sudo qubesctl state.sls qvm.anon-whonix
-
Note: Users should verify
saltcreates VMssys-whonixandanon-whonixbased on Whonix 14 templates. If problems are encountered such as the newly created VMs are Whonix 13 based.sys-whonixProxyVM andanon-whonixAppVM can be created manually from Qubes VM Manager. -
Users can verify
sys-whonixandanon-whonixVMs are based on Whonix 14 by listing the Debian aptsources.list. Newly created Whonix 14 VMs use Debian stretch (stable) as opposed to Whonix 13 VMs which use Debian jessie (old stable)In both
sys-whonixandanon-whonixVM konsoles, run.cat /etc/apt/sources.list.d/debian.listThe first 2 lines of output will show the following for Whonix 14 based VMs.
deb tor+http://sgvtcaew4bxjd7ln.onion stretch/updates main contrib non-free
deb http://security.debian.org stretch/updates main contrib non-free
Step 9: Copy the Whonix 13 Tor State to the newly created Whonix 14 (sys-whonix) VM. Users are encouraged to complete this step to maintain the same Tor entry guard and defend against tracking attempts by advanced adversaries.
Note: Steps to copy Tor state to secondary VM are in testing. Once complete, they will be added to the Whonix wiki. This will be completed shortly. Help welcome!
Please report any bugs in the Whonix forums so they can be addressed before the final Whonix 14 release.
It should be noted that users also have the option of doing an in-place upgrade of Whonix 13 to Whonix 14, rather than using the release candidate TemplateVMs. If this is preferable, follow the Testers-only documentation at the link below.
https://whonix.org/wiki/Upgrading_Whonix_13_to_Whonix_14
Detailed release notes for Whonix 14 can be found here: Changelog - Whonix
[1] https://www.whonix.org/wiki/Qubes/Update
[2] https://www.whonix.org/wiki/Dev/Qubes#salt
[3] https://www.qubes-os.org/doc/salt/