Hello. Usage of Whonix does hide the GPU name but doesn’t hide the CPU name and vendor. Is it possible to hide hardware from Whonix in order to make it more secure and decrease fingerprinting?
Yeah you can run it under QEMU full emulation mode if you can put up with the slow perf. No official support however:
Thanks, I will try it. But in practice, can destination website see the hardware information using remote JavaScript code or hardware info leak is only possible when Whonix Workstation is compromised?
Prerequisite reading, partially already answered on same link security-misc: Enhance Miscellaneous Security Settings.
CPUID is a mess and I don’t think there is any method to curb it.
Then then I found this cpuid x86 in JavaScript. but didn’t look into further.
Speculation: even if using security-misc: Enhance Miscellaneous Security Settings (or maybe even QEMU) it might still be possible to benchmark the browser to guess what hardware is being used and/or to fingerprint the browser. Using JavaScript. Or perhaps even without. For Tor Browser specific questions, I recommend, there is likely better information from Tor Project as per Free Support for Whonix ™.
Related:
They can perhaps get some idea by benchmarking your CPU with JS.
Is it worth to try to hide CPU info from applications inside Workstation? There might be a paradox: enabling hide-hardware-info.service can make you ‘a unique guy who uses hide hardware info’. Or not?
It is better not to hide CPU info but set up the most common CPU vendor and model in my opinion.
The less identifying info the better, if possible.
If there is a large userbase running it then it will end the paradox and provide safety in numbers.
Short of running a purely emulated CPU , there will be ways to benchmark and identify the hardware.
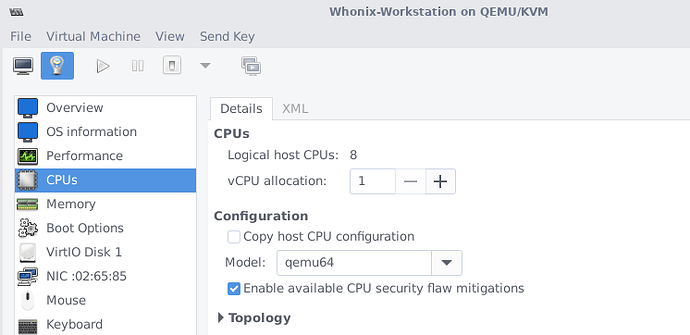
If you’re currently using Whonix for KVM and you’re using Virt-Manager, you can go to CPUs, disable host-passthrough and select qemu64.
If you prefer editing the XML:
<cpu mode="custom" match="exact" check="none">
<model fallback="forbid">qemu64</model>
<feature policy="require" name="ibpb"/>
<feature policy="require" name="md-clear"/>
<feature policy="require" name="spec-ctrl"/>
<feature policy="require" name="ssbd"/>
</cpu>
To be sure it worked check by running cpuid inside Whonix-Workstation before and after changing it. Your CPU model name should be QEMU Virtual CPU version 2.5+ after the change.
However, this could introduce vulnerabilities or attack surface, as it has not been researched yet, as mentioned below by Patrick.
This was discussed here:
Not safe without further research, pending todo tasks:
Very interesting info information I plan to look into this more.
Virtualbox is a type 2 hypervisor as compared to KVM which is a type 1 and imo in provides better protection but downside is it’s not user friendly compaired to Virtualbox though but thats off topic.