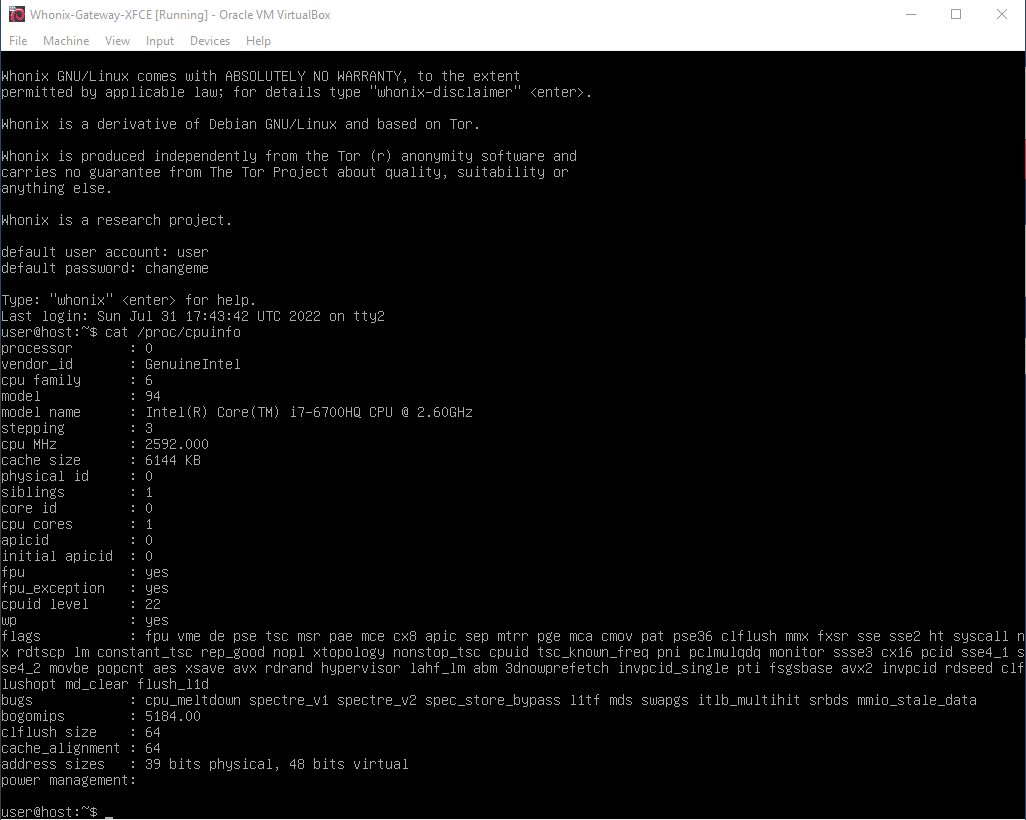
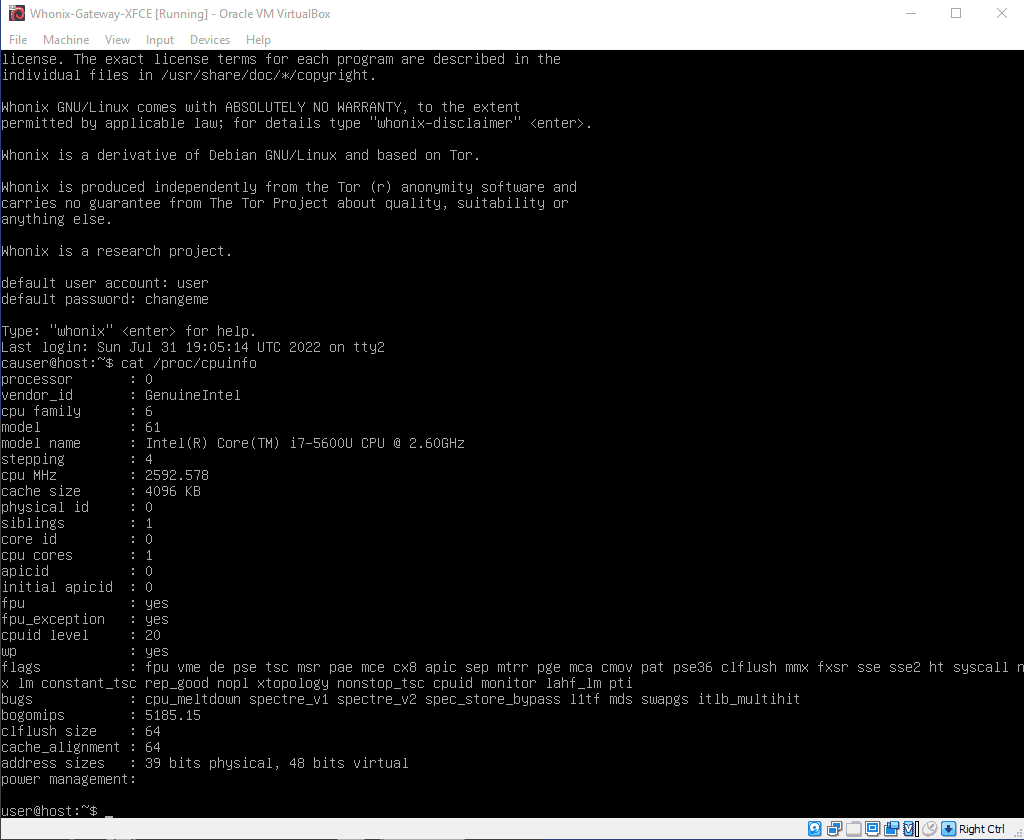
I was able to fake CPUID on VirtualBox using vboxmanage. Then I found https://phabricator.whonix.org/T408
Anyway, for the record:
set vm=“Whonix-Gateway-XFCE”
vboxmanage modifyvm %vm% --paravirtprovider none
vboxmanage modifyvm %vm% --cpuidremoveall
vboxmanage modifyvm %vm% --cpu-profile “Intel Core i7-5600U”