Here is the summarized and easily readable version of my Qubes-Whonix Tor Control Panel snowflake proxy installation fix/guide. The full version of my guide can be found at the bottom of the page.
Tired of your snowflake proxy not working in whonix? Follow the guide! ![]()
Qubes-Whonix Tor Control Panel with Working Snowflake Proxy [Quick Start Guide]
1) whonix-gateway-17 template terminal:
sudo nano /etc/resolv.conf.whonix
Replace “nameserver 10.0.2.3” with “nameserver 10.139.1.1(or the output of ip qubesdb-read /qubes-netvm-primary-dns run in a sys-whonix terminal, which should be 10.139.1.1, but if it is different, then use that output ip)”
Save & exit
2) whonix-workstation-17 template terminal:
qvm-copy-to-vm whonix-gateway-17 /var/cache/tb-binary/.tb/tor-browser/Browser/TorBrowser/Tor/PluggableTransports/snowflake-client
3) whonix-gateway-17 template terminal:
sudo cp ~QubesIncoming/whonix-workstation-17/snowflake-client /usr/bin/snowflake-client
sudo chmod og+rx /usr/bin/snowflake client
sudo nano /usr/share/anon-conection-wizard/bridges_default
Replace snowflake Bridges with:
Bridge snowflake 192.0.2.3:80 2B280B23E1107BB62ABFC40DDCC8824814F80A72 fingerprint=2B280B23E1107BB62ABFC40DDCC8824814F80A72 url=https://1098762253.rsc.cdn77.org/ fronts=docs.plesk.com,www.phpmyadmin.net ice=stun:stun.l.google.com:19302,stun:stun.antisip.com:3478,stun:stun.bluesip.net:3478,stun:stun.dus.net:3478,stun:stun.epygi.com:3478,stun:stun.sonetel.com:3478,stun:stun.uls.co.za:3478,stun:stun.voipgate.com:3478,stun:stun.voys.nl:3478 utls-imitate=hellorandomizedalpn Bridge snowflake 192.0.2.4:80 8838024498816A039FCBBAB14E6F40A0843051FA fingerprint=8838024498816A039FCBBAB14E6F40A0843051FA url=https://1098762253.rsc.cdn77.org/ fronts=docs.plesk.com,www.phpmyadmin.net ice=stun:stun.l.google.com:19302,stun:stun.antisip.com:3478,stun:stun.bluesip.net:3478,stun:stun.dus.net:3478,stun:stun.epygi.com:3478,stun:stun.sonetel.net:3478,stun:stun.uls.co.za:3478,stun:stun.voipgate.com:3478,stun:stun.voys.nl:3478 utls-imitate=hellorandomizedalpn
Save & exit
5) Shutdown whonix-gateway-17 template
6) Restart sys-whonix
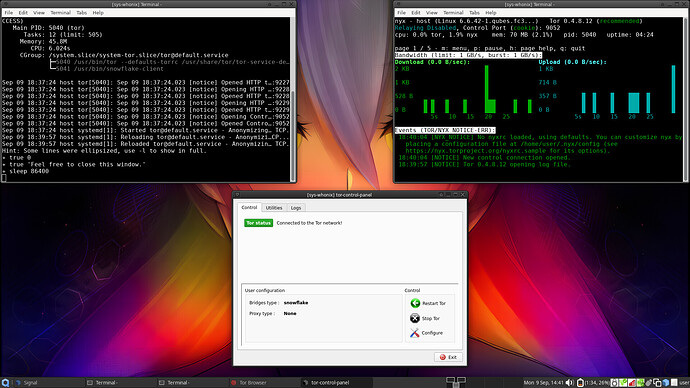
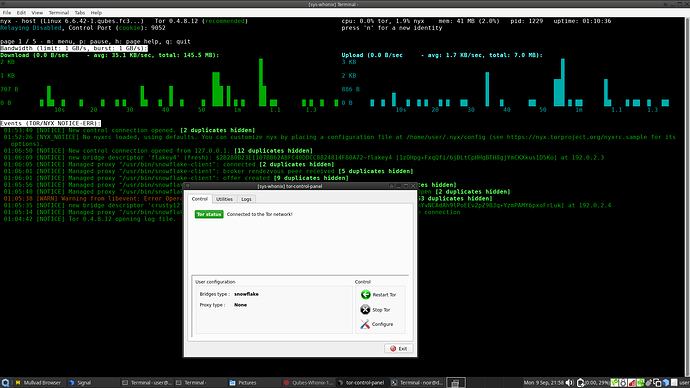
7) Start Tor Control Panel
Click Stop Tor
Click Configure
Select Bridges type: snowflake
Click Restart Tor
Enjoy Snowflake on Qubes-Whonix working the way it’s supposed to be! ![]()
Here is my original guide, on the Qubes-OS website:
Thanks to u/glockmane for summarizing the guide! ![]()