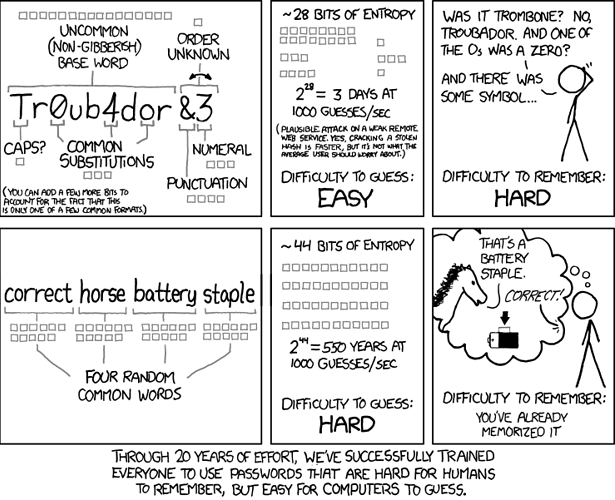
That article needs more contents.
- Suggest different password per website. Not password1, password2, Password alike variations. Explain why that is. Attackers use passwords which were leaked in one website as templates so they don’t have to fall back on “totally” brute force attacks.
- Don’t use online password generators for anything but curiosity / learning. That is because there is a very good chance the server could log them. The only place where passwords should be generated is locally, ideally in a VM without internet connection.
- We should distinguish between:
- passwords used at online services - these don’t need to be super long since the server rate limits how many passwords an attacker can try
- passwords used for offline encryption such as full disk encryption - the threat model here is different. An attacker can parallelize brute forcing the password and is only limited by available system resources. Much more guesses per second are possible.
Realistic scenarios would be great. Actionable advice as well. I would like our documentation to be useful for laymen not just geeks. I learned how non-geek laymen behave. Do you know some? Please try to discuss passwords with non-geek laymen so you know what I mean.
Partially password managers are a great idea. But how does one securely sync these with mobile devices? Suggesting to use unique super secure passwords for messengers etc. if these are supposed to be used on mobile as well would mean to type something like LMsy34z|'A~k/v3+n&trFU4b_T]3s.}4Uko^zra` on mobile. Unrealistic to expect.