Are the following assumptions correct?
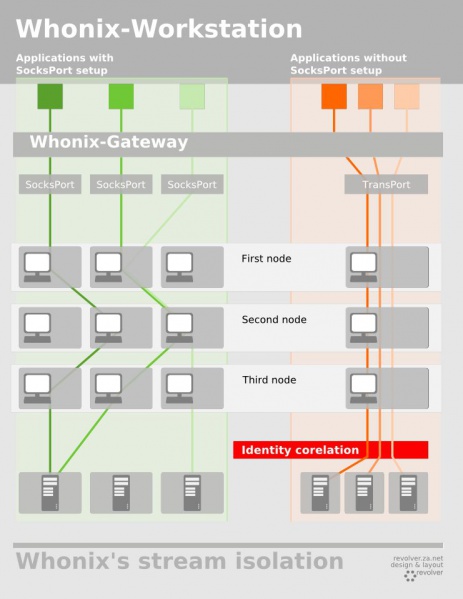
whonix-gw isolates traffic from whonix-ws by its SocksPort. This only works when software in whonix-ws is configured to use different SocksPorts (as outlined in the wiki: https://www.whonix.org/wiki/Stream_Isolation).
A VM not based on whonix-ws normally won’t utilize SocksPorts; whonix-gw will treat all traffic as it would with TransPort traffic from whonix-gw, i.e. it will as use the same circuit (while the traffic of each VM as a whole is isolated).
Now how would isolation by SocksPort need to be implemented for VMs not based on whonix-ws? Do they communicate with whonix-gw in the same way as whonix-ws? Would configuring an application to use a SocksPort be enough?
Does whonix-gw treat all non-proxied traffic as TransPort traffic and SocksPort traffic as, well, that?
I’m sure there’s is a clear answer to this somewhere in the wiki. However, I have been searching for it for quite some time without success. Is this documented anywhere?
Yes.
Yes. (Because of Tor’s IsolateClientAddr.)
Yes.
Traffic from Non-Qubes-Whonix-Workstation / Qubes whonix-ws based AppVMs not directed to a Tor SocksPort will use system default networking which will result in ending up in Tor’s DnsPort and TransPort.
Qubes-Whonix whonix-ws TemplateVM traffic wise works like an AppVM. Applications configured to use a Tor SocksPort do so. Other traffic using system default networking ends up in Tor’s DnsPort and TransPort.
Non-Qubes-Whonix-Gateway / Qubes sys-whonix by default has no system default networking. (But could be optionally enabled.)
( Whonix-Gateway Traffic: Transparent Proxying )
Does that answer your question?
It might not be documented. Please feel free to add it.
2 Likes
Thanks for confirming!
To isolate the traffic individual programs in a non-Whonix VM in Qubes I did the following:
-
Install torsocks without tor and its dependencies (libevent tor tor-geoipdb), e.g. manually in aptitude.
-
Get the IP address of sys-whonix by running ip route show.
-
Edit /etc/tor/torsocks.conf so that the corresponding lines read:
-
TorAddress 10.137.3.1 (or whatever IP address ip route show returns)
IsolatePID 1
Now every command executed with torsocks should be relayed through an isolated stream. This is also what happened when I tried to run torsocks curl ipinfo.io multiple times.
The isolation will only be as good as torsocks is. But any leaks will be relayed though that VM’s main Tor stream, just as the traffic of any program not launched through torsocks.
Btw aptitude is not required for that.
sudo apt-get install --no-install-recommends torsocks
(And anon-ws-disable-stacked-tor [reboot required] might work as well as
per
Whonix Packages for Debian Hosts and Whonix Host Enhancements)
1 Like