Telegram has used really weak encryption in the past and most people haven’t realised that those issues have been solved with MTProto 2. Some people also dislike that Telegram uses their own home-made encryption rather than using something like the Signal protocol which has been audited many times and is well respected by cryptographers.
Is telegram fully Open Source nowadays or is there some trickery involved?
Does The Reasons Why You Should Not Use Telegram Open Source Code (still?) apply?
That’s indeed a crux in context of Tor / Whonix.
Telegram is where many people who have been censored by private companies go nowadays and use it as a “hard”-to-censor [1] notification mechanism to reach their audience or modern replacement (IRC alike) chat channel. It looks very popular outside the Tor / Whonix sphere.
I would use Telegram to get the word out if I was censored [i.e. beyond already existing self-censorship] by private companies too. (At least for communications on subjects other than Tor / Whonix.) Even if there were “Open Source trickery issues”, which are really bad indeed, it does its job currently to provide free speech.
Related:
[1] I cannot personally say if telegram censors nothing, light, or whatnot since I did not research that in depth. From what I causally observed it looks like one of the most free speech supporting platforms at the momment.
The clients are all open source but the server is proprietary.
I’m not sure but that doesn’t seem to affect users. It looks to be something that will only affect developers and people wanting to make their own Telegram fork.
I think they only censor porn in public groups unrelated to porn.
Telegram code base is shoddy and allow RCE or months:
Telegram does not activate its secret chat by default which the creator defends but is irrelevant to our threat model:
The new protocol has not been audited either.
That vulnerability required the user to manually run malware someone sent them. All this bug did was help disguise the malware as a photo. The bug was also fixed quickly and there haven’t been many other important ones. I don’t think it deserves to be called shoddy.
Giving cwtch a go and will document it once it works.
Install golang from backports. Version in stable is too old.
Install git from stable.
go get cwtch.im/cwtch
cd /home/user/go/src/cwtch.im/cwtch/
go run app/cli/main.go
2020/06/29 21:11:08 cli/main.go [ERR ]
Error connecting to Tor: 510 Unrecognized command: Command filtered
exit status 1
On the website it says:
A Tor daemon running with the following configuration is currently also needed to run Cwtch:
SOCKSPort 9050 ControlPort 9051
Is it a matter of just enabling the ricochet profile on onion grater? Are the ports the same? Are extra steps needed to redirect traffic?
NVM I just remembered that the underlying ricochet protocol was broken the last time we tested and this the likely explanation.
Could be yes if it’s same Tor control protocol commands. If different, then onion-grater profile changes would be required.
These ports are properly emulated already, yes.
Dunno. bindp was required for applications that open a server inside the workstation on localhost only but that actually would need to listen on workstation external interface to be reachable from Tor on gateway.
Great news. It works after enabling the grater profile I am now able to create a profile.
The process itself has bugs that cause the program to crash but that has nothing to do with Tor connectivity.
Welcome to Cwtch!
If this if your first time you should create a profile by running/new-profile
/load-profileswill prompt you for a password and load profiles from storage
/helpwill show you other available commands
There is full [TAB] completion supportcwtch> /new-profile
Error creating New Profile, usage: /new-profile [name]
cwtch> /new-profile anon
** WARNING: PASSWORDS CANNOT BE RECOVERED! **
Enter a password to encrypt the profile:
Re-enter password: 2020/07/01 15:11:33 app/app.go [DBUG] CreatePeer(anon)
cwtch> 2020/07/01 15:11:33 v1/profile_store.go [DBUG] eventHandler()!
2020/07/01 15:11:33 app/applets.go [DBUG] appletPeers LaunchPeers
2020/07/01 15:11:33 app/applets.go [DBUG] Launching xxxx
2020/07/01 15:11:33 peer/cwtch_peer.go [DBUG] cwtchPeer Listen sending ProtocolEngineStartListen
2020/07/01 15:11:33 app/applets.go [DBUG] done Listen() for xxxx
2020/07/01 15:11:33 app/applets.go [DBUG] done StartPeersConnections() for xxxx
2020/07/01 15:11:33 app/applets.go [DBUG] done StartGroupConnections() for xxxxLoaded profile anon (xxxx)
1 profiles active now
You should runselect-profileto use a profile orlist-profilesto view loaded profiles
panic: runtime error: invalid memory address or nil pointer dereference
[signal SIGSEGV: segmentation violation code=0x1 addr=0x58 pc=0x662e34]goroutine 22 [running]:
git.openprivacy.ca/openprivacy/connectivity/tor.(*torProvider).Listen(0xc0000887e0, 0x72aec0, 0xc00000eae0, 0x2696, 0x0, 0x0, 0x0, 0x0)
/home/user/go/pkg/mod/git.openprivacy.ca/openprivacy/connectivity@v1.1.2/tor/torProvider.go:176 +0x424
cwtch.im/tapir/networks/tor.(*BaseOnionService).Listen(0xc000088310, 0x7e7c80, 0xc000092480, 0x0, 0x0)
/home/user/go/pkg/mod/cwtch.im/tapir@v0.1.18/networks/tor/BaseOnionService.go:129 +0xb2
cwtch.im/cwtch/protocol/connections.(*engine).listenFn(0xc0004ca0c0)
/home/user/go/src/cwtch.im/cwtch/protocol/connections/engine.go:206 +0x76
created by cwtch.im/cwtch/protocol/connections.(*engine).eventHandler
/home/user/go/src/cwtch.im/cwtch/protocol/connections/engine.go:167 +0xe46
exit status
Briar is probably the best Tor/Whonix messaging app option…
- Private Messaging, Private Groups, Blogs, Forums, RSS Feeds, more
- Decentralized Peer-2-Peer Tor Hidden Onion Services (no central servers)
- Anonymous Identities (hides contact metadata)
- End-2-End Encryption with Forward Secrecy (including encrypted metadata)
- Secure Remote Contact Adding/Exchanging
- Anti-Censorship Capabilities (alternative no-internet network routing over Bluetooth or Wi-Fi)
- Free and Open Source
- Independent Security Audit in 2017
- Ongoing Active Development
- Ease of Setup / Ease of Use
- Android and Linux supported (Linux version in open beta release right now)
- Also useful for communicating to more mainstream non-Linux & non-Desktop based people
About Briar:
“Briar is a messaging app designed for activists, journalists, and anyone else who needs a safe, easy and robust way to communicate. Unlike traditional messaging tools such as email, Twitter or Telegram, Briar doesn’t rely on a central server - messages are synchronized directly between the users’ devices. If the internet’s down, Briar can sync via Bluetooth or Wi-Fi, keeping the information flowing in a crisis. If the internet’s up, Briar can sync via the Tor network, protecting users and their relationships from surveillance.”
“Briar has received funding from Small Media, the Open Internet Tools Project, Access, the Open Technology Fund, the Prototype Fund, Internews, the NLnet Foundation, the Next Generation Internet programme and the ISC Project.”
Great article explaining Briar advantages over other messaging apps:
Briar homepage:
Briar how it works:
Briar features & how to use:
https://briarproject.org/manual
Briar wiki article:
Briar animated-gif screenshot of some features and interfaces:
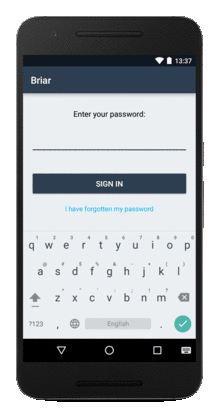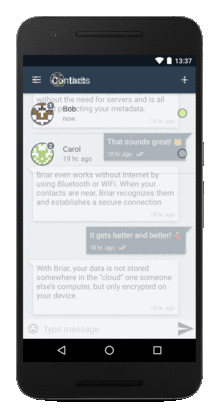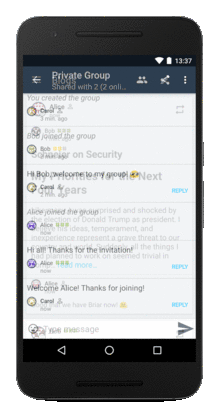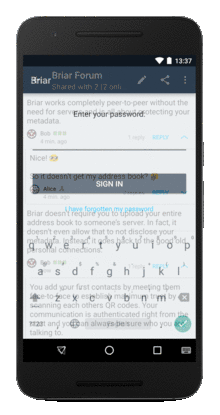
Briar Linux Desktop version info and links:
Briar Linux Desktop developer announcements blog:
Briar Android download:
Briar News blog:
https://briarproject.org/news
Briar Twitter page:
https://nitter.net/BriarApp
https://twitter.com/BriarApp
The ability for widespread, uncompromising, open source, P2P anonymous & E2E encrypted direct messaging with fellow techies and mainstream people, on both desktop and mobile platforms, is an awesome benefit that is here with Briar.
It would be great to see Briar incorporated into Whonix by default! ![]()
Definitely. I’ve known about it for some time, but you’ve really got us excited over it with this news.
That was only for a beta release.
The results are still impressive though. Would be great to have another audit for the stable release.