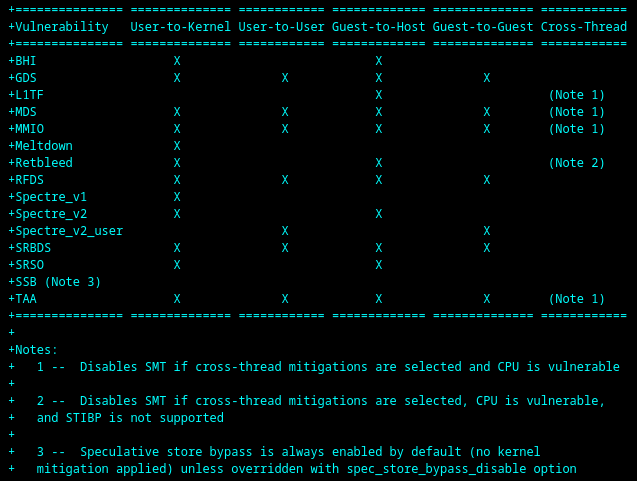
Code:
+=============== ============== ============ ============= ============== ============
+Vulnerability User-to-Kernel User-to-User Guest-to-Host Guest-to-Guest Cross-Thread
+=============== ============== ============ ============= ============== ============
+BHI X X
+GDS X X X X
+L1TF X (Note 1)
+MDS X X X X (Note 1)
+MMIO X X X X (Note 1)
+Meltdown X
+Retbleed X X (Note 2)
+RFDS X X X X
+Spectre_v1 X
+Spectre_v2 X X
+Spectre_v2_user X X
+SRBDS X X X X
+SRSO X X
+SSB (Note 3)
+TAA X X X X (Note 1)
+=============== ============== ============ ============= ============== ============
+
+Notes:
+ 1 -- Disables SMT if cross-thread mitigations are selected and CPU is vulnerable
+
+ 2 -- Disables SMT if cross-thread mitigations are selected, CPU is vulnerable,
+ and STIBP is not supported
+
+ 3 -- Speculative store bypass is always enabled by default (no kernel
+ mitigation applied) unless overridden with spec_store_bypass_disable option
Image:
Markdown Table:
| Vulnerability | User-to-Kernel | User-to-User | Guest-to-Host | Guest-to-Guest | Cross-Thread |
|---|---|---|---|---|---|
| BHI | |||||
| GDS | |||||
| L1TF | [1] | ||||
| MDS | [1:1] | ||||
| MMIO | [1:2] | ||||
| Meltdown | |||||
| Retbleed | [2] | ||||
| RFDS | |||||
| Spectre_v1 | |||||
| Spectre_v2 | |||||
| Spectre_v2_user | |||||
| SRBDS | |||||
| SRSO | |||||
| SSB[3] | |||||
| TAA | [1:3] |
Disables SMT if cross-thread mitigations are selected and CPU is vulnerable ↩︎ ↩︎ ↩︎ ↩︎
Disables SMT if cross-thread mitigations are selected, CPU is vulnerable, and STIBP is not supported ↩︎
Speculative store bypass is always enabled by default (no kernel mitigation applied) unless overridden with
spec_store_bypass_disableoption ↩︎