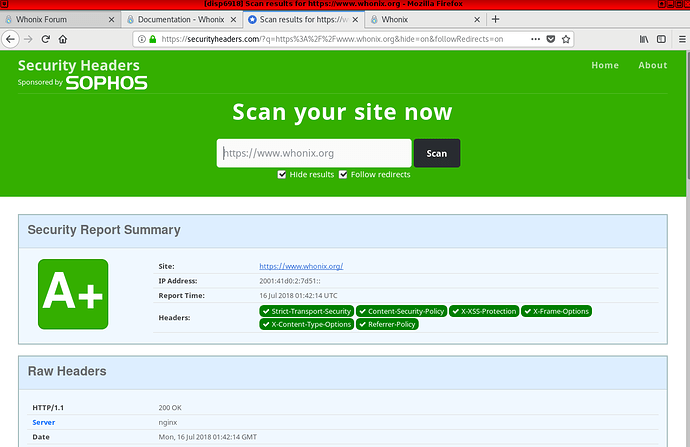
Good news! We’ve implemented Content-Security-Policy headers on various areas of the Whonix infrastructure.
This includes the main site, the wiki, this forum, and a few other places.
We also implemented Referrer-Policy and some other headers in recent weeks.
We now get an A+ rating on the main page at https://securityheaders.com \o/
Some things to note:
-
We deliberately are not allowing loading images from third party sites on the forum and also in the wiki. If you find your hotlinked Wikipedia, Imgur, etc is not loading: that’s a feature, not a bug. @Patrick’s request.
-
Some apps such as the wiki, the forum etc, regrettably still involve the use of unsafe-inline for some javascript/css. This is due to the design of the third party software these apps run, and forking in order to fix is not practical. Where you find that securityheaders.com caps the site to ‘A’ instead of ‘A+’, it’s likely due to the use of unsafe-inline.
Both Discourse and MediaWiki have upstream tickets to look at shipping with a decent CSP. Phabricator recently added one, so we are using the default one there.
Nonetheless, even with some limited use of unsafe-inline, a CSP is better than none at all, and where possible with simple cases of javascript (such as on the main page, and in Mailman/Pipermail interfaces) we have used the sha256 technique to avoid having to fall back to unsafe-inline.
We ran with these CSPs for about week in ‘Report-Only’ mode, so we’re pretty confident things were looking OK in order to activate these for real. Of course:
- if you find any pages on any areas of the whonix.org infra that are totally broken, and
- the ‘Console’ tab of your browser debugger identifies this as a Content-Security-Policy issue, and
- it’s not a case of a hot-linked image, font, etc, which quite deliberately is a violation of our chosen policy
…then please mention it here and I can take a look.
The various CSPs we’ve deployed, should significantly enhance the safety for users when browsing the Whonix.org public sites, including on .onion.
We’ll continue to assess and tune the CSPs as needed.
Any questions, just reply!
Cheers!