Too bad, that Qubes-Whonix users do not fully benefit much from the recent user/root/misc hardening by Whonix by default such as for example:
- Restrict root access
- protect Linux user accounts against brute force attacks
- GitHub - Kicksecure/security-misc: Kernel Hardening; Protect Linux User Accounts against Brute Force Attacks; Improve Entropy Collection; Strong Linux User Account Separation; Enhances Misc Security Settings - https://www.kicksecure.com/wiki/Security-misc
- Kernel Hardening - security-misc
- Linux Kernel Runtime Guard (LKRG)
- Strong Linux User Account Isolation
- And possibly also soon Untrusted Root - improve Security by Restricting Root.
- documented here:
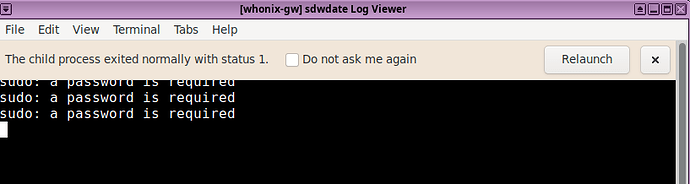
Preventing malware from gaining root is vital to prevent malware from breaking out of a VM, spreading to dom0 or other VMs. Many attacks aren’t possible with root and/or kernel level compromise.
(More meaningful separation of root and kernel is being worked on.)
This is currently really bad in Qubes Debian templates. Any compromised user (not only user user) can use su without a password and gain root. (bug reported here)
Just learned that qubes-template-debian-10-minimal comes without passwordless root by default. This is documented here:
Minimal templates | Qubes OS
Quote:
It is an intentional design choice for Passwordless Root Access in VMs to be optional in Minimal TemplateVMs. Since the Minimal TemplateVMs are minimal , they are not configured for passwordless root by default. To update or install packages, execute the following command in dom0 (where
Xis your distro and version number):[user@dom0 ~]$ qvm-run -u root X-minimal xtermThis opens a root terminal in the Minimal TemplateVM, from which you can use execute root commands without
sudo. You will have to do this every time if you choose not to enable passwordless root.If you want to be able to use
sudoinside a Minimal TemplateVM (or TemplateBasedVMs based on a Minimal TemplateVM), open a root terminal as just instructed, then install thequbes-core-agent-passwordless-rootpackage.Optionally, verify that passwordless root now works by opening a normal (non-root) xterm window in the Minimal TemplateVM, then issue the command
sudo -l. This should give you output that includes theNOPASSWDkeyword.
In Qubes Debian minimal templates user user is also by default not a member of group sudo.
This is an excellent basis for Qubes-Whonix.
(Which is already based on Qubes Debian minimal templates.)
Qubes-Whonix package qubes-whonix-shared-packages-recommended currently Depends: on qubes-core-agent-passwordless-root. This dependency could be dropped.
The question is, how users could easily gain root then. In dom0 command line:
qvm-run -u root X-minimal xterm
Or
qvm-run -u root X-minimal xfce4-terminal
Usability issue. Which may be fixable. More on that below.
Security issue? Better than the default we have now. However, I am not sure if that is non-ideal security wise. Running a GUI application as root? Maybe a better default would be if a user admin would be a member of group sudo by default? Then open a terminal as user admin and allow admin to use sudo without a password?
Usability. Somehow add a Qubes start menu entry. Not sure that is yet supported by Qubes to run something as a different user from Qubes start menu.
Example:
dom0
cat .local/share/qubes-appmenus/debian-10/apps.templates/xfce4-terminal.desktop
[Desktop Entry]
…
Exec=qvm-run -q -a --service – %VMNAME% qubes.StartApp+xfce4-terminal
We’d have to use qvm-run -u admin. That may require Qubes dom0 enhancements.
If these aren’t coming / too late, maybe we could work around that limitation somehow. Perhaps an /etc/sudoers.d exception. Maybe a dom0 yes/no prompt using qrexec.